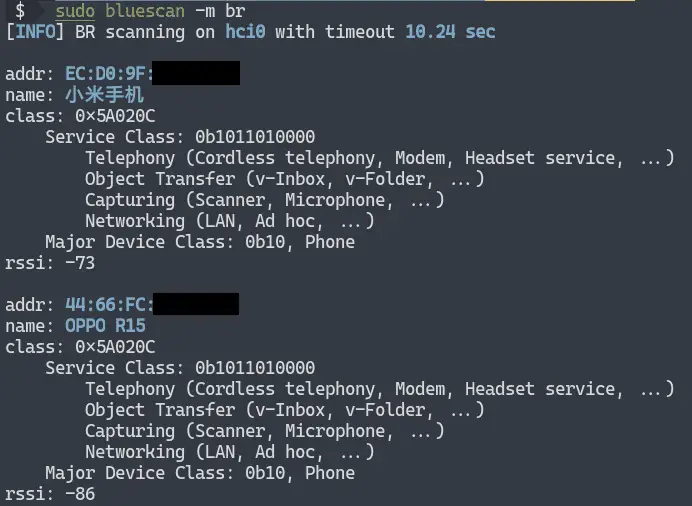
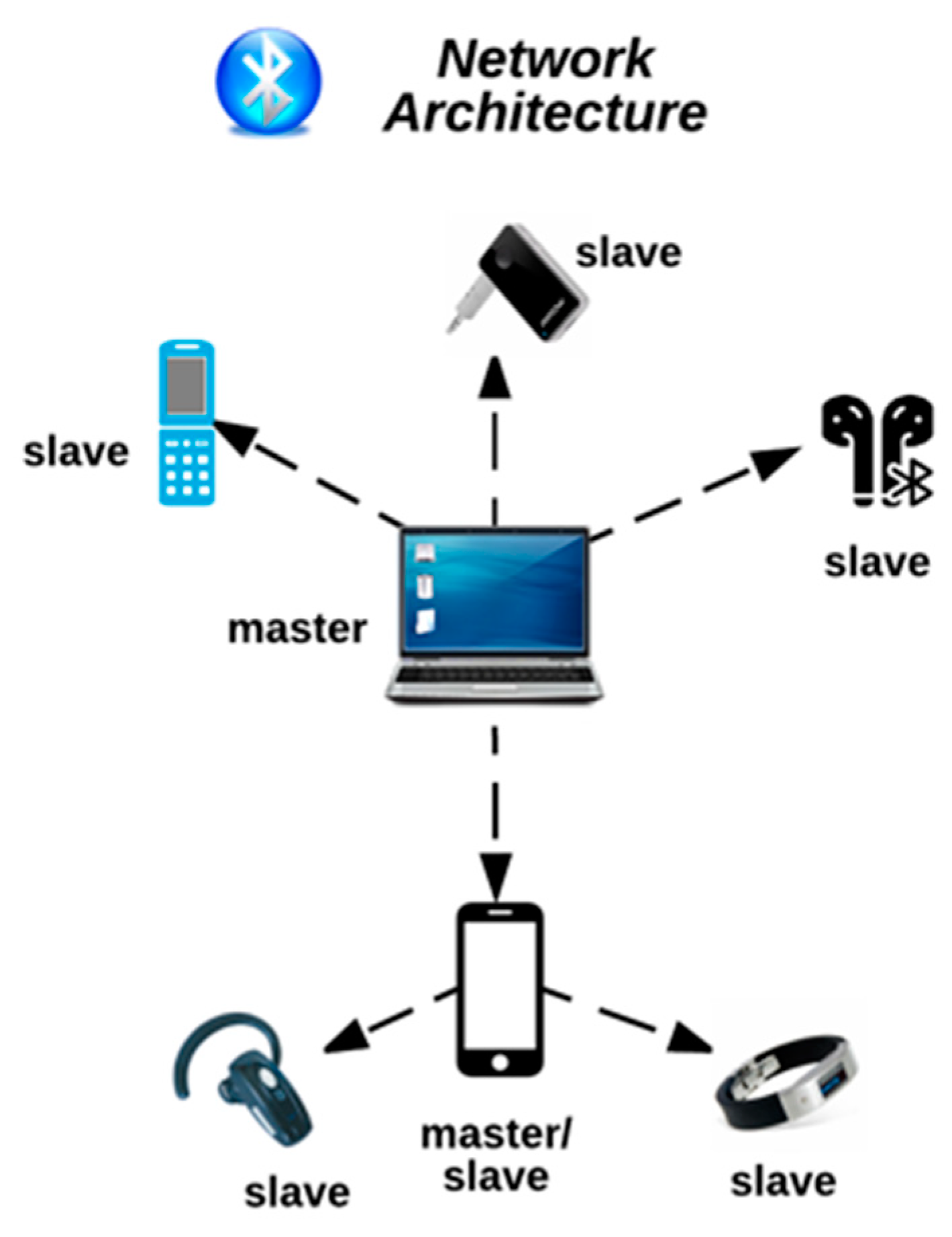
Bluetooth vulnerability can be exploited in Key Negotiation of Bluetooth (KNOB) attacks | Malwarebytes Labs

BleedingTooth: Google drops full details of zero-click Linux Bluetooth bug chain leading to RCE | The Daily Swig
BLURtooth Attack - A Bluetooth Vulnerability To Overwrite Authentication Key - Hackers Online Club (HOC)